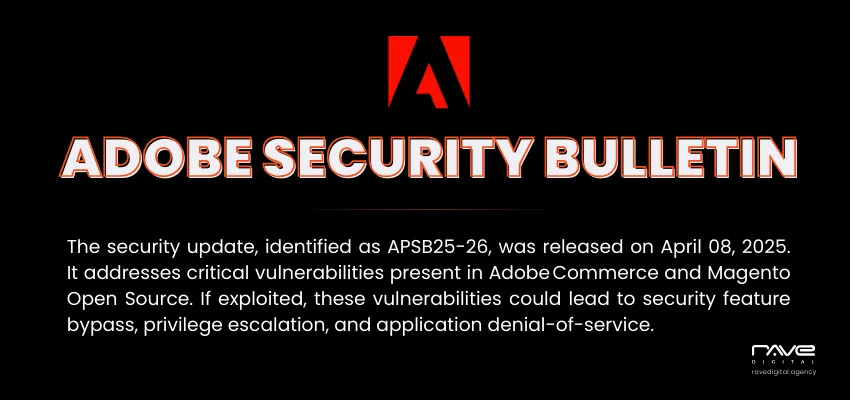
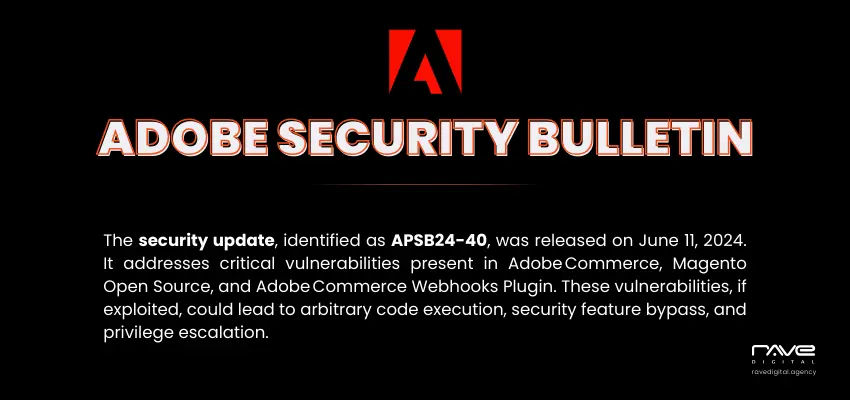
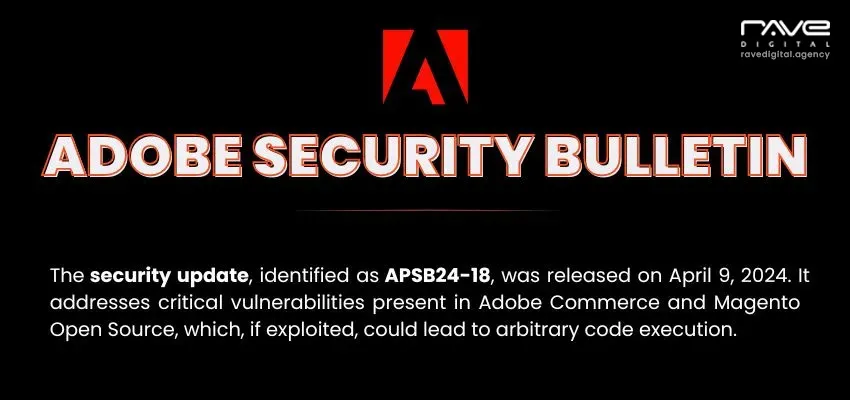
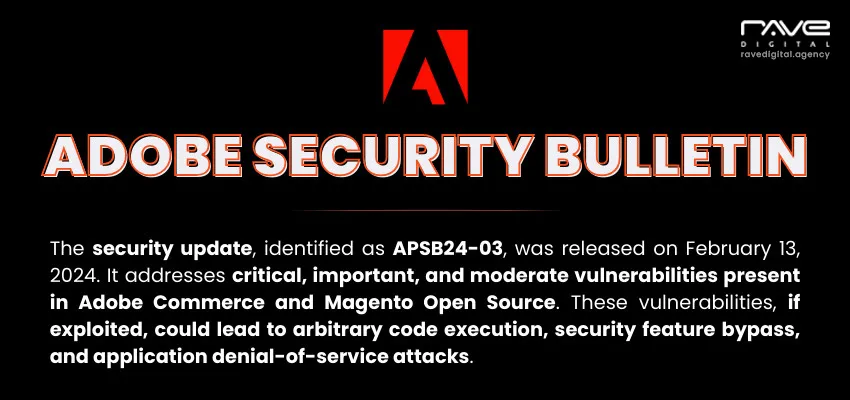
Despite being one of the most robust ecommerce platforms, Magento presents some security related issues to the users. And this is why Magento timely releases new versions and security patches aimed to guard against these vulnerabilities.
Magento has released the latest security updates primarily for Magento Commerce and Open Source 2.3.0, 2.2.7 and 2.1.16. The versions contain multiple security enhancements that help close Remote Code Execution (RCE), Cross-Site Scripting (XSS) and other vulnerabilities.
- Magento Commerce and Open Source 2.3.0
- Magento Commerce and Open Source 2.2.7
- Magento Commerce and Open Source 2.1.16
- Magento Commerce 1.14.4.0
- Magento Open Source 1.9.4.0
- SUPEE-10975 to patch earlier Magento 1.x versions
There were several high CVSSv3 Severity issues found which affected the products Magento Open Source prior to 1.9.4.0, and Magento Commerce prior to 1.14.4.0, Magento 2.1 prior to 2.1.16, Magento 2.2 prior to 2.2.7. Below are the few bugs:
Issue Type: Remote Code Execution (RCE)
| CVSSv3 Severity | Security Bug | Description |
| 9.1 | PHP Object Injection (POI) and Remote Code Execution (RCE) in the Magento 2.1.15 Admin | An administrator user with access to the Braintree payment method configuration can trigger remote code execution through PHP object injection. |
| 9.1: | PHP Object Injection (POI) and Remote Code Execution (RCE) in the Admin | An administrator with access to Varnish configuration settings and the design configuration can trigger remote code execution through PHP object instantiation. |
| 8.8 | Remote Code Execution through Path Traversal | Administrators with limited privileges can upload an unauthorized template using the path traversal capability. |
| 8.5 | Remote Code Execution through the Admin | A user can upload unauthorized files while creating a downloadable product. |
| 8.5 | Remote Code Execution in Upload of Quote File | The upload settings for B2B quote files are vulnerable to remote code execution attacks. |
| 8.5 | Remote Code Execution Vulnerability in Race Condition | An unauthorized file download can be used to remotely execute code. |
| 8.5 | API-Based Remote Code Execution Vulnerability | By activating an API that supports the ability to add products, a malicious user can send base64-encoded content to an unauthorized file and use it to remotely execute code. |
| 8.5 | API-Based Remote Code Execution Vulnerability | By activating an API that supports the ability to add products, a malicious user can send base64-encoded content to an unauthorized file and use it to remotely execute code. |
Issue Type: Privilege Escalation
| CVSSv3 Severity | Security Bug | Description |
| 7.7 | Unauthorized read permissions through Email Templates | A malicious user could use special characters in this content to circumvent the CSS directive that allows the CSS file to be loaded directly to the body of the content. |
| 7.2 | Bypass of Authorization Check by Unauthorized Users | An unauthorized user can access user data by rendering arbitrary code blocks. |
| 6.5 | Vulnerability in Customer Shopping Cart | The customer shopping cart and coupons are vulnerable to cross-site scripting attacks |
Issue Type: Cross-Site Request Forgery (CSRF)
| CVSSv3 Severity | Security Bug | Description |
| 6.5 | Customer Gift Card Vulnerability | Customer gift cards are vulnerable to brute-force and cross-site request forgery attacks during redeem a gift card and check balance and sales actions. |
| 6.5 | Vulnerability within Return Order Requests | Return merchandise authorizations (RMA) are vulnerable to cross-site request forgeries. |
| 6 | Remote Code Execution through the Product Media Upload in the Admin | A path traversal vulnerability permits folder creation at arbitrary locations and file deletion from arbitrary locations in the Admin product image/media upload area. |
Source: Magento
It is highly recommended by Magento to deploy these new releases right away, to ensure optimal security and performance. Remember to implement and test the patch in a development environment first to confirm that it works as expected or consult a professional.
What else can be done to protect a Magento site?
Apart from installing the security patches, you can always ask Magento certified professionals to conduct a security audit every quarter to ensure that your store is secured especially if you have installed new extensions and made some changes to the site.
If you’re interested in implementing the security patches or to upgrade your Magento site, reach out to Rave to quickly schedule a meeting with one of our Certified Magento Professionals who will coordinate a free Upgrade Assessment and estimate.